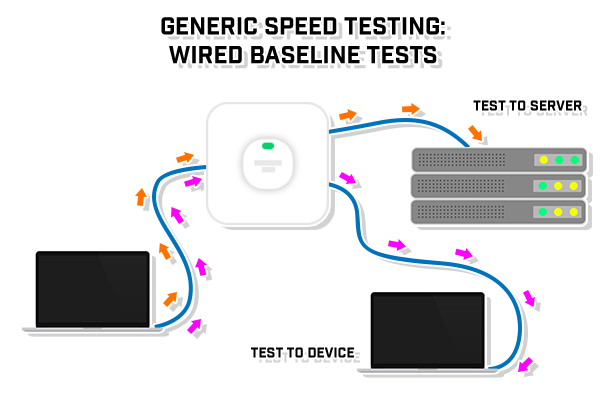
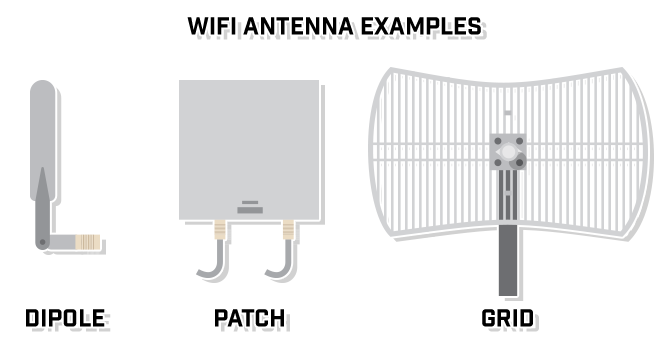
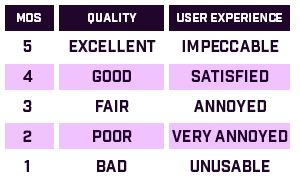
Whether building a new network or upgrading one, generic speed testing is a must. It is important to have testing controls to create baselines so that true and expected speeds can be properly evaluated. Use proper software for this testing, such as iPerf or WiFiPerf / WiFiPerf Professional as well as something like fast.com to tests internet speeds from different servers around the world.
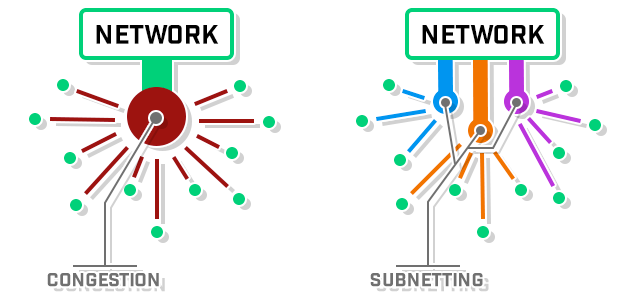
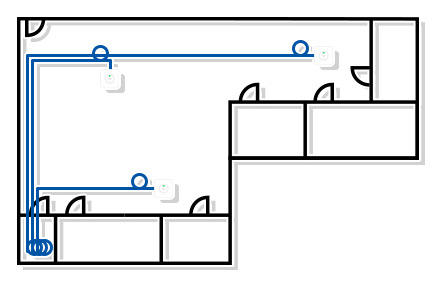
Let's start with some definitions.