An intrusion detection system (IDS) monitors network devices in order to grant security administrators the ability to identify attacks in progress and take appropriate action to protect a network. In order for users on a network to access a web server on the internet, the firewall must allow traffic through port 80. However, this open port is often used as an attack vector for hackers and malware to gain access to your network. An IDS examines this traffic and compares it with known exploits; similar to how antivirus software uses known virus signatures to identify threats. When the intrusion system detects a match to a known exploit, it sends an alert to the security or web server administrator so they can take action. Intrusion prevention systems (IPS) are very similar to IDSs, but as opposed to just sending an alert, these systems go one step further and automatically take action to prevent an intrusion.
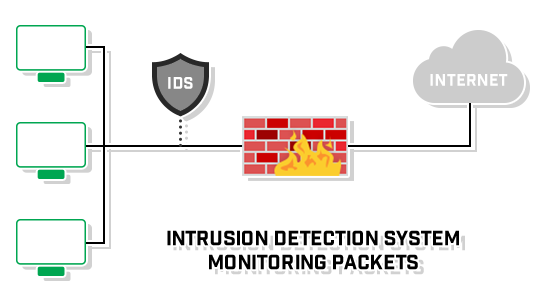
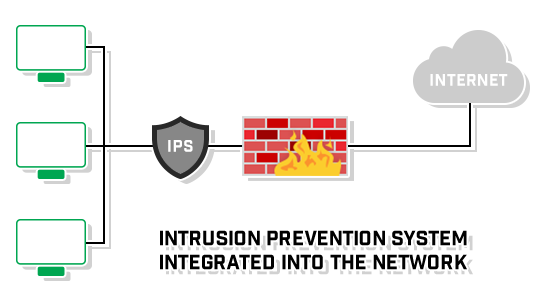 So, you’re probably wondering why anyone would use an intrusion detection system when an intrusion prevention system will actively protect your network.
So, you’re probably wondering why anyone would use an intrusion detection system when an intrusion prevention system will actively protect your network.
Well, there are two main categories of these systems: passive and active. A passive system, like an IDS, will only monitor, log, and provide alerts to activity, while an active system will automatically take action based on software design. In an active system, like an IPS, innocent traffic can be seen as malicious and, therefore, will be blocked from the network, causing false positives. A false positive on an IDS will be less detrimental to a network since an administrator can see that the traffic is actually innocent and will not completely cut connection just because the system thinks that the traffic is a little suspicious.
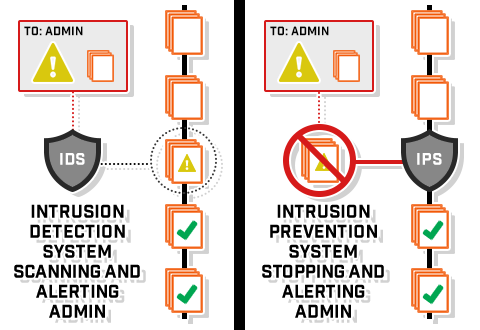
Of course, the time from the start of an attack to the time a network is compromised can be mere milliseconds, which is way too fast for any human to react with the correct action. Therefore, vendors have started to focus on bettering IPSs and even incorporating prevention features in IDSs. An active IDS just sniffs traffic and can be turned off or unplugged from the network without affecting network connectivity. However, an IPS is inline, making it more capable of stopping malicious traffic than an active IDS, especially against UDP-based attacks. Many current IDSs include IPS features and often have optional modules, such as malware detection and Web filtering, in an attempt to remedy the drawbacks of an IPS. Most IDSs and IPSs have built-in anomaly-detection capabilities that work by establishing a baseline of normal activity on a network and then send an alert if any activity significantly deviates from this baseline.
Intrusion detection and prevention systems keep networks secure and require the expertise of an administrator to set up, run, and maintain. In smaller companies, when a security event happens, usually administrators clean up the mess and report the event to management, the legal department, or even law enforcement. Security information and event management tools can help network administrators identify attacks and indicators of compromise by collecting, aggregating, and correlating log and alert data from routers, firewalls, IDS/IPS, endpoint logs, web filtering devices, honeypots, and other security tools. Bringing these alerts together from every device on a network can give a security-monitoring administrator or analyst context to make better informed decisions on how to strengthen the network.